Strategy through Execution
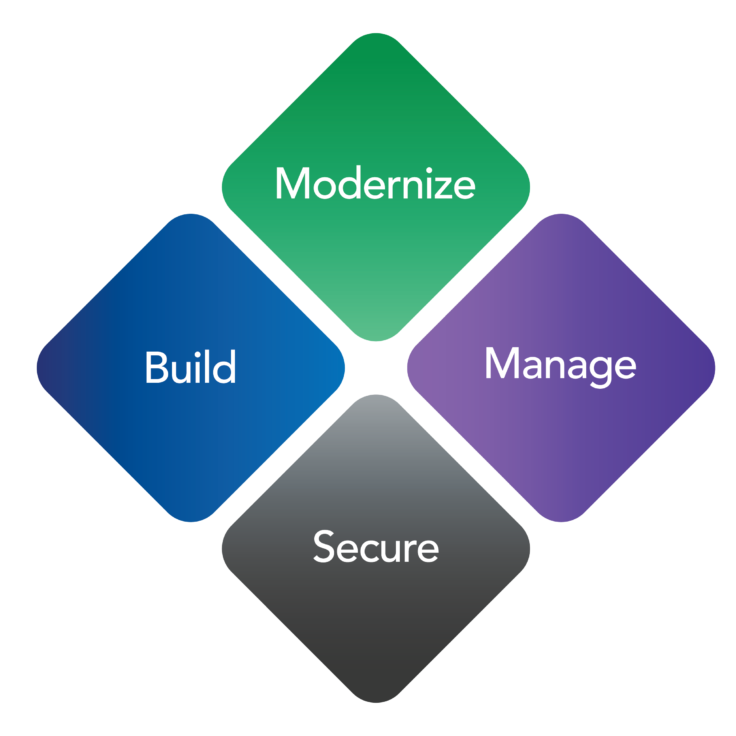
Operating across four interlocking principles – Build, Modernize, Manage and Secure – Forty8Fifty Labs delivers modern technology solutions for today’s digital business. Our engagements follow a proven strategic methodology for results that align with your business goals.